Introduction to OpenPGP
The term OpenPGP has been used on this website without explaining what it mean. OpenPGP is the most widely used email encryption standard in the world. It is defined by the OpenPGP Working Group of the Internet Engineering Task Force. The OpenPGP standard was originally derived from PGP (Pretty Good Privacy), first created by Phil Zimmermann in 1991.
One of the great advantages is that it doesn’t depend on one specific digital signature algorithm, or digital encryption algorithm, and hence it is sustainable throughout different times.
If you want a more detailed reason for using OpenPGP for businesses, refer to Focus on secure communication: Why you should sign and encrypt your emails. And if you want a more technical explaination, the GNU Privacy Handbook is recommended reading.
Key exchange
The foundation for OpenPGP evolve around something called public key infrastructure (PKI). This mean that the key used to encrypt a message isn’t the same as used to decrypt it, as it would be using an ordinary lock in daily life, technically this is called asymmetrical key encryption. The equivalent of an ordinary lock is symmetrical key encryption.
The reason for this is amongst other things that you can safely transmit the locking key, referred to as a public key. While you still keep the unlocking key, the private key. So you make the public key available for everyone, but only you keep the private key yourself.
It is important to understand that this mean that if you want to communicate securely with another party, that party will need to have a compliant system as well (installed the appropriate applications). This isn’t a technical problem, it is a social problem. It is usually easiest to start with yourself configuring OpenPGP. Then a friend configure it and you two can communicate securely and sign eachother’s keys. Then you slowly expand your Web of Trust.
Keyservers
In order to make exchanging keys easier, a series of key servers for OpenPGP have been configured around the world. These keyservers are storing massive amounts of keys, and synchronises between eachother. Instead of having to send your key to everyone already having your OpenPGP Public key if someone new signs it, you upload it to a keyserver and people refreshes your key from there from time to time.
This can either be done from the graphical user interface, and is generally called refreshing the keys, or if using GnuPG you can manually issue the command "gpg –keyserver x-hkp://pool.sks-keyservers.net –ref" , I add the –keyserver option in here as I don’t know if you already have a keyserver configured in the configuration file. You can add the line "keyserver x-hkp://pool.sks-keyservers.net" in gpg.conf in order to not have to type it every time. the gpg.conf file is not created by default, so if you don’t find it, create it. It should be located in ~/.gnupg/ on unix-like systems and if using an NT based windows, it can be found at %appdata%gnupg (just type this into the address bar in microsoft explorer. For win9x the ordinary location is the same same as the folder containing gpg.exe
The Web of Trust
Now, simply having the public key of a person isn’t enough, as anyone can create a keyset with any data and upload it to a keyserver. This is why you should verify with the person that it indeed is their own key. Now, this is very easy if it is a friend that you can just call and verify the key id and fingerprint, and recognize by voice that it is the correct person. Or if it is a business associate and you get to see his driver’s license, and note down the key id and fingerprint. But if it is someone more distant it gets more difficult. That is where the Web of Trust comes into play
To show yourself and others that you have verified that another person’s public key in fact belong to the person, and hence confirmed the identity of the owner, you digitally sign the other person’s key. You may, or may not, trust that the other person properly verify and sign keys, but if you believe that the individual does, you can use the digital signature verification again to verify your own trust.
Why all this? Now, if someone trust you to properly verify keys, they can know that your friend is who he claims he is, by looking at your digital signature in his or her public key. They don’t have to go through the work of verifying the key, you have already done so.
Ok, that got a little bit complex, so let us illustrate it with a graph.
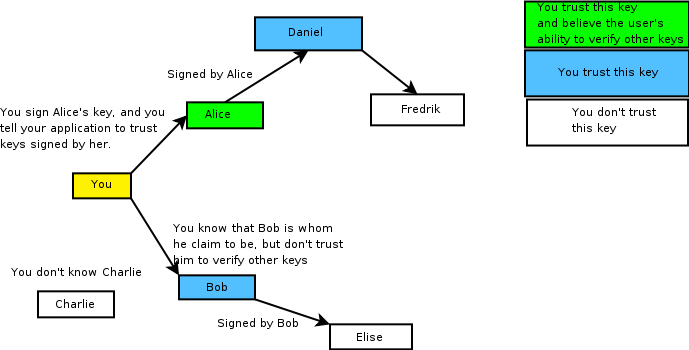
Now, it is important to understand that whether you decide to trust Alice to sign other keys or not is a personal matter, and other’s won’t see it. Hence if Alice trust Daniel to sign keys, you still won’t trust Fredrik.
So, why does this matter? Well, since one of the goals is verifying that emails come from the person that it claim it come from, you need to be able to see if the key belong to the actual person.
Key note
I usually carry the details necessary to exchange key information with me in my wallet in case I meet someone who potentially will communicate securely with me.
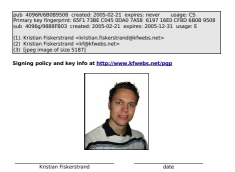
It provide the key size and type, the key identification number, the date it was created, the usage for the key and the fingerprint of the primary key, as well as the different user identification strings attached to the key, the picture ID, as well as fields for me to enter the date and my signature.
Now, the most observative of you might notice that it list two, and not one key id and size. In my case a primary key of ID 0x6B0B9508 used for Cerification and Signing, and a subkey with the usage of Encryption. The reason for this is, beside technical reasons to use different keys for signatures and encryption, that you will usually want the signing key to last for a while (or in my case forever) while you might want to change the encryption key once in a while.
I usually change the encryption key once a year to show that my key is active. One reason for this is that you can’t encrypt messages to keys which are expired, and you will therefore have to refresh the key, either by downloading it from my website or by refreshing it from a PGP Keyserver. If my key has been compromised in any way, I will by that time have revoked it, and you will stop sending emails that might be read by others. Of course once a year might be too seldom, so I suggest people refresh their keyring once in a while to get updates.
Business card
Granted walking around with a self-printed key note might not be the best option to give to potential business prospects. But what about printing your OpenPGP key id and fingerprint on a business card? That way people who knows what OpenPGP is can communicate with you securely, while others will most likely just ignore it.
My business card ends with the following two lines:
PGP: 0x6b0b9508
65F1 73BE C045 0DA0 7A58 6197 16E0 CF8D 6B0B 9508
This easily fits on a standard 87mm x 49mm size business card.